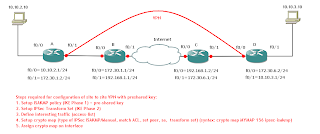
In this topology I have 4 routers, 2 of them simulating internet (B and C), 2 of them are VPN peers (A and D). I have static routes defined for simplicity. Before start to configure the VPN we need to verify that we can reach peer IP addresses (172.30.1.2 and 172.30.6.2) from router A and D, but we cannot reach 10.10.2.1 neither 10.10.3.1.
|
At this point I'll save the config files and name them: a-confg-u, b-confg-u…
u will means Unconfigured :P
After I have the IP of the interfaces and routing configured, I’ll keep the configuration only with routing configured, so next time I’ll not play to configure interfaces and routes. I will only switch the configuration files in the net file. This way I’m planning to improve my configuring speed when the time for the big lab exam will come. Also there I’ll keep the network diagram, and in the diagram at the bottom, I’ll write few remarks/guides. I’ll upload all the net files, all config files only with routing, the finished config files and my diagrams as well. Hope someone will find them useful in the future. I’m sure that I’ll find them useful after 6-9 months :P
I have decided not to write detailed steps how to configure all the steps. You can find that information everywhere, and I don't see any point to make a copy paste from the console. Those posts are meant to be used 1-2 weeks before the CCSP exams, and 1-2 months before the LAB exam. I think there might be exceptions of the configurations that are long and hard to remember.
Steps required for configuration of site to site VPN with preshared key:
- Setup ISAKMP policy (IKE Phase 1) + pre-shared key
- Setup IPSec Transform Set (IKE Phase 2)
- Define interesting traffic (access-list)
- Setup crypto map (type of IPSec ISAKMP/Manual, match ACL, set peer, sa, transform set) (syntax: crypto map MYMAP 156 ipsec-isakmp)
- Assign crypto map on interface
_____________________________________________
After the configuration you should try to ping from router A or D with source address from 10 network:
| D#ping 10.10.2.10 source fa0/1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.2.10, timeout is 2 seconds: Packet sent with a source address of 10.10.3.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = |
Useful show commands:
- show crypto isakmp sa
- show crypto ipsec sa
- show crypto map
- show crypto session
- debug crypto isakmp
- debug crypto ipsec
The biggest “trouble” I had here was to remember the syntax of step number 4, therefore I added the syntax into the picture diagram above.
The config files with final configuration will be named: a-confg and d-confg.
Files which will be uploaded:
- vpn-pre-shared-key.doc
- vpn-pre-shared-key-small.png
- vpn-pre-shared-key.net
- a-confg-u, b-confg-u, c-confg-u, d-confg-u (conf files with routing configured)
- a-confg, d-confg (working VPN config).
UPDATE: I have added a capture and a few wireshark screenshots
There you can see 6 ISAKMP Phase 1 packets, and 3 Quick mode
Phase 2 packets. First 2 ISAKMP packets are policy negotiation.
Second pair ISAKMP packets are DH Exchange.
3rd pair is Identity information's exchange (pre-shared key)
This is the first encrypted packet.
Phase 2 (Quick mode) is done in 3 packets:
1. Requestor sends IPSec SA proposal, with optional info if
Perfect Forwards Secrecy (PFS) will be used.
2. Responder check the proposal and sends back an answer
3. Requestor send an confirmation that SA have been negotiated
After this process the data encryption will start.
Plans for the future post:
To be made analyses with unsuccessful connections.
You can get them from here:
http://sites.google.com/site/cciesecurityattempt/Home/vpn-pre-shared-key.zip
to be uploaded: vpn-pre-shared-key-cap.zip

No comments:
Post a Comment