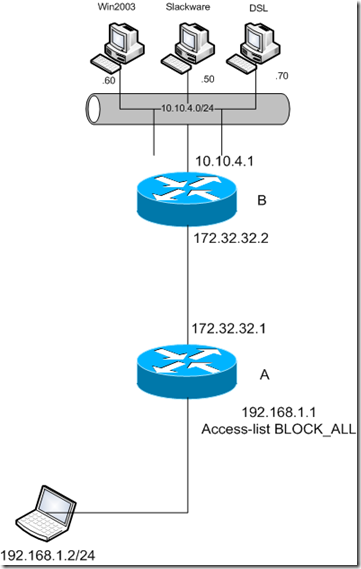
Here we have very similar topology as previous example. The difference is that we have added card NM-1FE-TX on router B, and we connected virtual windows 2003 server which will play the role of CA server. IP address assigned to the server is 10.10.4.60. We have installed support for SCEP protocol on that server as well. You can download for free (something free from Microsoft? Amazing, isn't it? :-) ) from here: http://download.microsoft.com/download/c/e/e/ceef4ccf-b603-4790-bd9e-f112c3270d2e/cepsetup.exe
Also we have added static routes to the 10.10.4.0/24 network to the routers that needed to reach the CA server. Before to start with configuration, we have to verify that we can reach CA server from all the routers, and that we cannot reach 10.10.3.0/24 network from router A, neither 10.10.2.0/24 network from router D.
After the installation of capsetup.exe file on the CA server, we will get the URL for SCEP enrollment. You need to write it down. In my case is: http://jas-uvjdckpdvov/certsrv/mscep/mscep.dll (What a strange name for a windows server, isn't? :-) At this point all the configuration files are named as: x-confg-u, where x is the router name.
We need to do a bit of preparation before start to configure the peers. We need to make sure that the time and date are the same on the VPN peers as well on the CA server. Probably for this lab the most handy will be to setup CA as ntp server, but I wasn't able to find out how to do that from Windows help :( Also we need to configure domain name, ip host for CA server, and to generate the rsa keys for both peers.
First of all we need to request certificate from a CA. I have experienced some issues during this process, and I'll try to explain them here. After we have configured time and date, domain name, generated rsa keys, and assign an ip host for the CA server, we can continue to the configuration:
The trustpoint name can be something more reasonable, as long it is defined with correct IP address as ip host. I just wanted to be on the safe side here :-) At this point we have defined the URL for SCEP enrollment.
2nd step is to authenticate to the CA. Here is where I have done the mistake, typing my own password. The syntax is:
A(config)#crypto pki authenticate jas-uvjdckpdvov
Certificate has the following attributes:
Fingerprint MD5: 396C1E3F 9BDC2D71 641E5077 4E5ADC0D
Fingerprint SHA1: 2EF2F253 B502F445 0EFC947E 2674FD7F A50A76E1 % Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted. A(config)#crypto pki enroll jas-uvjdckpdvov
%
% Start certificate enrollment ..
% Create a challenge password. You will need to verbally provide this password to the CA Administrator in order to revoke your certificate. For security reasons your password will not be saved in the configuration. Please make a note of it. Password: password
Re-enter password: password % The subject name in the certificate will include: A.darkside.net
% Include the router serial number in the subject name? [yes/no]: yes
% The serial number in the certificate will be: 3B843B84
% Include an IP address in the subject name? [no]:
Request certificate from CA? [yes/no]: yes
% Certificate request sent to Certificate Authority
% The 'show crypto ca certificate jas-uvjdckpdvov verbose' command will show the fingerprint. .Oct 16 01:09:58.735: CRYPTO_PKI: Certificate Request Fingerprint MD5: 5B8E4A75 6320D376 18BB0461 87ED9DFF
.Oct 16 01:09:58.743: CRYPTO_PKI: Certificate Request Fingerprint SHA1: C9620276 3EB6CCC5 D8D6D241 1C931DF5 FD946901
.Oct 16 01:10:01.823: %PKI-6-CERTREJECT: Certificate enrollment request was rejected by Certificate Authority |
We need to get the password from CA in order our request to be approved. It is stored at: http://localhost/certsrv/mscep/mscep.dll and it is valid for 60 minutes, and it can be used only once, which means you need to refresh that page when you enroll router D :-) After that we should get this wonderful syslog message:
| Oct 16 01:17:25.179: %PKI-6-CERTRET: Certificate received from Certificate Authority. |
We are almost good to go now. We just need to configure isakmp policy, transform set, crypto map and access list, and to assign the crypto map to the VPN peer interface. Sooo easy :-). I have made another mistake on the access list here. Stupid me... I have created access lists in format: "permit ip any <remote network>", and "permit ip <remote network> any" on both routers. That costs me additional 30 minutes staring at both configurations of the routers, running debug, even raising SDM hoping that it will tell me something more. All that I got were only those very strange lines in the syslog:
Oct 16 01:29:54.055: IPSEC(validate_transform_proposal): no IPSEC cryptomap exists for local address 172.30.6.2
Oct 16 01:29:54.059: ISAKMP:(0:1:SW:1): IPSec policy invalidated proposal
Oct 16 01:29:54.063: ISAKMP:(0:1:SW:1): phase 2 SA policy not acceptable! (local 172.30.6.2 remote 172.30.1.2)
Oct 16 01:29:54.067: ISAKMP: set new node 1138201416 to QM_IDLE
Oct 16 01:29:54.075: ISAKMP:(0:1:SW:1):Sending NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 1705632040, message ID = 1138201416 |
You can easy simulate this, by just deleting one line from the access list in the working configuration, and allow ip any any as 2nd line of that access list.
Oct 16 00:02:11.291: map_db_find_best did not find matching map
Oct 16 00:02:11.295: IPSEC(validate_transform_proposal): no IPSEC cryptomap exists for local address 172.30.6.2
Oct 16 00:02:11.299: ISAKMP:(0:1:SW:1): IPSec policy invalidated proposal
Oct 16 00:02:11.303: ISAKMP:(0:1:SW:1): phase 2 SA policy not acceptable! (local 172.30.6.2 remote 172.30.1.2) |
After changing the access-lists in the format: "permit ip <local net> <remote net>", "permit ip <remote net, local net>" finally I got the ping response from the remote network.
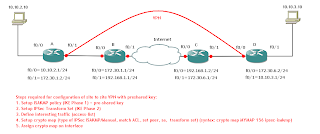
Configuration steps for this lab:
1. Set correct time and date, domain name, rsa keys, and assign a ip host for a CA
2. Define the trustpoint, and enrolment mode and url
3. Authenticate on the CA
4. enroll for certificate, with the correct password :-)
You can get the usual files from here:
http://sites.google.com/site/cciesecurityattempt/Home/vpn-pki.zip
TO BE UPLOADED: vpn-pki.cap, vpn-pki-cap.png