This looks quite simple. All what we need to do is to configure a tunnel interface, and to point a route to the destination network with gateway the tunnel interface. We are using the same topology as for PKI deployment, and the same config-u files for start.
| interface Tunnel0
ip address 172.31.1.1 255.255.255.252
tunnel source FastEthernet0/1
tunnel destination 172.30.6.2 ip route 10.10.3.0 255.255.255.0 Tunnel0 |
From now on, I'll include simple captures in the zip file.
You can get the files from here:
http://sites.google.com/site/cciesecurityattempt/Home/vpn-gre.zip
Update:
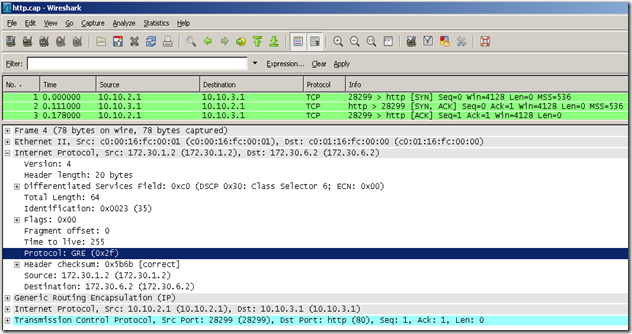
I have made a capture of an http connection between the routers, where you can clearly see GRE in action. The filename is http.cap, and the screenshot is named http-cap.png. Check the source and destination IP addresses, before encapsulation and after the GRE encapsulation. Also I have played a bit with tunnel interfaces. I have changed the IP address of the tun0 interface of router A to 169.254.254.254/24, and left the same IP address on router D and the tunnel was still working. If you remove the IP address of the tun0 interface, you'll not be able to bring up the tunnel.
Conclusion: The tunnel interfaces must have an IP address assigned, but they don't have to be in the same subnet in order for the tunnel to be brought up.